Connecting a GCP Account
To connect a GCP organization to OpsHelm, follow the steps below.
Start the onboarding process
- First, go to the Accounts page in the dashboard.
- On the Accounts page, click the
Add Organizationbutton, and selectGCPunder Cloud Provider.
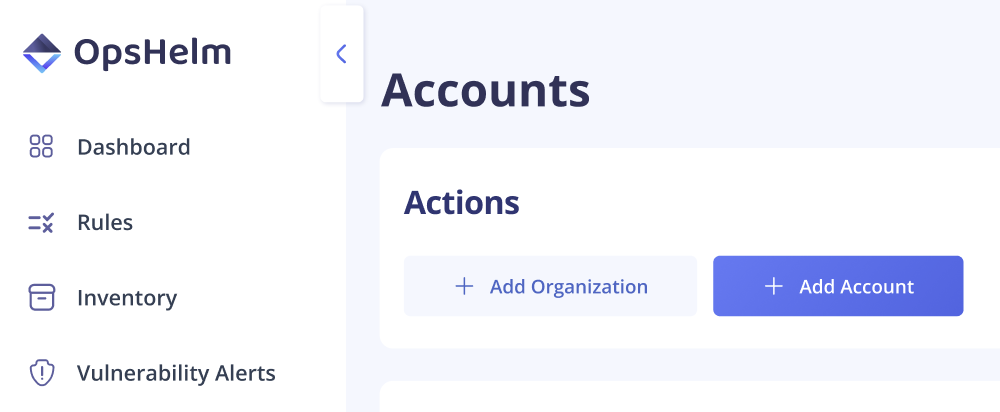
- In the onboarding modal, select the GCP logo, enter a Display Name and numeric GCP Organization ID.
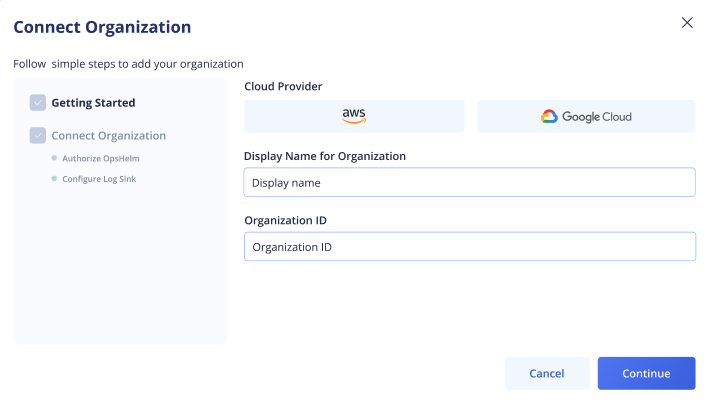
Your organization ID can be found by logging into the GCP Web Console, and clicking on the project picker in the top left corner
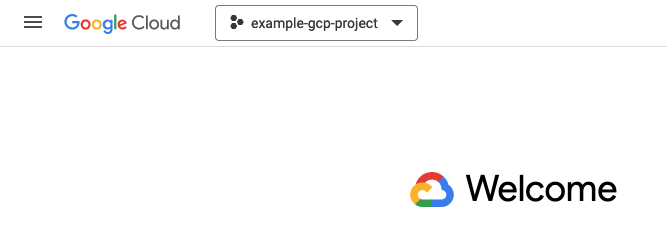
Then looking for your organization in the list (it will be the entry with an office building icon, and will have a numeric ID), in this example the Organization ID would be 123456789012.
Alternatively you can use the gcloud command to find your Organization ID, by using the gcloud organizations list command.
Once you have entered the details, click continue to begin the onboarding process.
Authorize OpsHelm
Once the onboarding process is started, you will need to authorize OpsHelm to connect to your GCP account.
OpsHelm requires read-only access to the “Asset Inventory” in your environment via the predefined cloudasset.viewer role, and read-only permission to list projects within your organization via the predefined browser role.
To ease the process of onboarding we will generate a service account for this purpose and ask you to grant that account access to the appropriate roles. This will be displayed on the user interface. The easiest way to acheieve this is using the gcloud command:
gcloud organizations add-iam-policy-binding <YOUR_ORG_ID_HERE> --member=<OPSHELM_SERVICE_ACCOUNT_HERE> --role=roles/cloudasset.viewer --include-children
gcloud organizations add-iam-policy-binding <YOUR_ORG_ID_HERE> --member=<OPSHELM_SERVICE_ACCOUNT_HERE> --role=roles/browser --include-children
Both of these role are read-only roles and do not provide OpsHelm any write permissions to your environments.
The --include-children flag ensures that this is applied to all projects within your organization, to avoid the need to enable each environment individually, if you wish to add environments individually this flag can be omitted.
Configure Log Sink(s)
In order for OpsHelm to receive the appropriate logging information for your environment, you need to configure a log sink which forwards to our pub/sub queue, you can use the following gcloud command for this:
gcloud logging sinks create opshelm-log-sink pubsub.googleapis.com/projects/definitely-not-prod/topics/logsink-<CUSTOMER_ULID_HERE> --include-children --log-filter 'protoPayload.@type="type.googleapis.com/google.cloud.audit.AuditLog" AND SEVERITY>="NOTICE"' --organization=<YOUR_ORG_ID_HERE>
The filter applied to this command ensures that logs are restricted to GCP generated logs only, not logs that you generate from within your own applications, and that only those with a severity of NOTICE or above are collected.
The --include-children flag ensures that this is applied to all projects within your organization, to avoid the need to enable each environment individually, if you wish to add environments individually this flag can be omitted.
Audit Logs
If audit logs are not already enabled within your organization, you should enable them by visiting:
https://console.cloud.google.com/iam-admin/audit/allservices?organizationId=<YOUR_ORG_ID_HERE>
Without logging enabled, OpsHelm will not be able to receieve updates regarding your environment